
What’s Your Risk in Dollars? Why You Need FAIR or Equivalent Models
Stop guessing. Start quantifying. Because “high risk” doesn’t mean anything—until it has a price tag.

Stop guessing. Start quantifying. Because “high risk” doesn’t mean anything—until it has a price tag.
Cybersecurity leaders love to talk about risk. High risk. Critical risk. Medium-low-maybe risk. But ask what that means in dollars—real financial impact—and most can’t answer.
That’s the problem with qualitative risk scoring. It’s subjective, inconsistent, and unhelpful when it’s time to justify budgets, prioritize work, or explain exposure to the board.
If you want to treat cybersecurity as a business function, you need business metrics. That means moving to quantitative risk modeling, and the gold standard is FAIR—the Factor Analysis of Information Risk model.
Heat maps. Risk matrices. Red-yellow-green scores. They feel familiar. But they don’t:
Worst of all, they don’t translate to dollars. And that’s the language executives and boards speak.
Without financial context, every risk looks “high,” and every investment is hard to justify. You end up with check-the-box security, not cost-effective security.
FAIR is a structured, repeatable model for quantifying risk in financial terms. It replaces guesswork with data-driven estimates. Here’s how it works at a high level:
You input ranges, not perfect numbers. FAIR uses probability distributions to estimate the Annualized Loss Expectancy (ALE)—the expected cost per year of a given risk scenario.
You walk away with a dollar figure, not a color.
You might think quantitative models are for big banks or Fortune 100s. Wrong. Mid-sized companies actually benefit more—because:
FAIR helps you prioritize by business impact, not buzzwords. Whether you’re debating EDR vendors, training programs, or new controls, FAIR gives you a risk-reduction-per-dollar metric you can defend.
Let’s say your phishing risk model estimates:
That’s $225K per year in expected loss. Now compare:
Your net exposure drops to ~$33K. That’s a $192K reduction for a $75K investment.
This is the kind of math your CFO will approve. Because it’s not security for security’s sake—it’s risk transfer with a measurable return.
FAIR isn’t the only way to quantify risk—but it’s the most widely adopted, NIST-recognized, and open-standard model available. And it’s flexible enough to scale from simple spreadsheet models to integrated risk platforms.
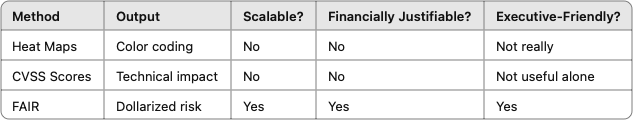
FAIR isn’t the only way to quantify risk—but it’s the most widely adopted, NIST-recognized, and open-standard model available. And it’s flexible enough to scale from simple spreadsheet models to integrated risk platforms.
If you have limited resources and need to make smart decisions, quantifying risk is no longer optional—it’s foundational.
You don’t need a full GRC suite or $100K consulting engagement. You can start with:
Within days, you can be modeling ransomware, phishing, cloud misconfigurations, or insider risk with credible, actionable numbers.
Boards don’t fund vague risk. CFOs don’t approve fear. And regulators don’t care how colorful your heat map is.
They want to know: What’s the risk in dollars? What are we doing about it? Is it enough?
FAIR and other quantitative models give you the answer. They turn cybersecurity into a financial conversation—and put you in control of that conversation.
Because at the end of the day, risk that can’t be measured can’t be managed. And it definitely can’t be defended.